What is the UpGuard Breach Risk vulnerabilities module?
Learn about what the vulnerabilities module of UpGuard Breach Risk is, CVSS, CVE IDs, and more.
The vulnerabilities module in UpGuard Breach Risk lists vulnerabilities identified from information exposed in HTTP headers, website content, and open ports.
As UpGuard scans from outside companies’ networks, there are some vulnerabilities we can confirm (verified vulnerabilities), but others we only know may exist based on the version of the software detected (unverified vulnerabilities).
When verified vulnerabilities are detected, you’ll see them in your risk profile and be able to use them in our remediation and risk waiver workflows, just as you can with other risks.
Another indicator to look for is the "known" label, which indicates that the vulnerability is on CISA's list of known exploited vulnerabilities. Unverified but known exploited vulnerabilities should be investigated to determine whether these systems are likely to exploited or not.
When you have confirmed that unverified vulnerabilities do not apply to a system– like when they have been patched but the software version not yet upgraded– you can remove them from the displayed list by using the "Ignore vulnerabilities" button. This is different from a risk waiver because you are signaling that the risk doesn’t exist, as opposed to a risk waiver where you are accepting the risk.

What is the difference between an unverified and verified vulnerability?
When we identify that one of your websites is running a specific software version that has known vulnerabilities, we are often unable to verify whether the vulnerability exists. Rather, we can only verify that it may exist based on the exposed information, but could also be mitigated by a patch that does not change the detectable software version.
This is also why unverified vulnerabilities appear as informational through other parts of UpGuard, such as on your risk profile or during risk remediation workflows.
In contrast, for some vulnerabilities, we can run a specific test that is able to confirm the domain is vulnerable to that vulnerability. The details of each test are unique to each CVE.
In short, unverified vulnerabilities may be exploitable and therefore appear as informational risks while verified vulnerabilities are exploitable and have risk classifications.
How to filter vulnerabilities
To filter vulnerabilities, select Apply filters.

This will cause a panel to slide out from the right side of your screen. In the panel, you can filter by label, verified status, CVE ID, software, CVSS severity, and EPSS score. When you are happy with your selection, select Apply.

How to ignore an unverified vulnerability
To ignore an unverified vulnerability click Ignore Vulnerabilities in the top right corner of the vulnerabilities table.

Once clicked, your screen will change allowing you to select the vulnerabilities you want to ignore. Select the vulnerabilities you want to ignore by clicking the checkbox to the left of the CVSS column.

When you’re done, select Ignore vulnerabilities.

If you want to find a specific vulnerability, click on the search box and search by its CVE ID.

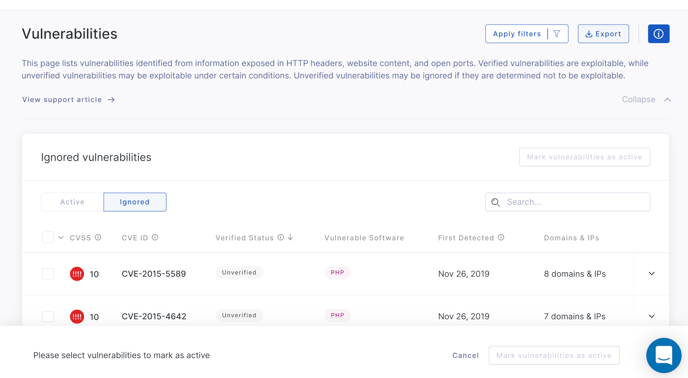
How to remove an unverified vulnerability from the ignored list
To remove an ignored unverified vulnerability, head to Vulnerabilities and select the Ignored tab.

Then select Mark vulnerabilities as active.
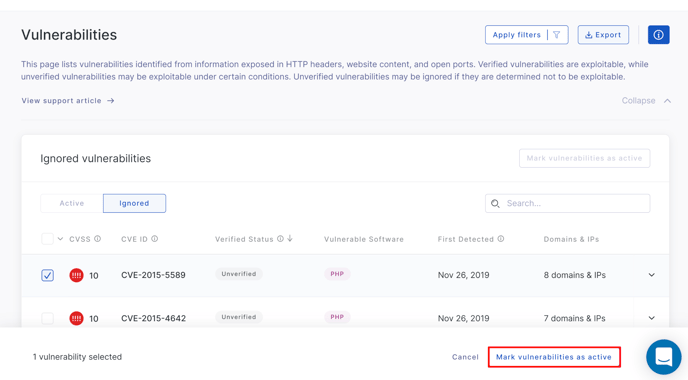
Once clicked, your screen will change allowing you to select the vulnerabilities you want to mark as active. Select the vulnerabilities you want by clicking the checkbox to the left of the CVSS column.
When you’re done, select Mark vulnerabilities as active.
If you want to find a specific vulnerability, click on the search box and search by its CVE ID.

What is a CVE ID?
Each vulnerability in CVE is described as a known vulnerability or exposure and is given a standard identifier number with status indicator (i.e. "CVE-1999-0067", "CVE-2014-12345", "CVE-2016-7654321"), a brief description and references related vulnerability reports and advisories.
Each CVE ID is formatted as CVE-YYYY-NNNNN. The YYYY portion is the year the CVE ID was assigned or the year the vulnerability was made public.
Unlike vulnerability databases, CVE entries do not include risk, impact fix or other technical information.
We show each vulnerability CVE ID in the UpGuard platform.
What is CVE?
The vulnerabilities reported in the Vulnerabilities section of UpGuard Breach Risk have been published to the Common Vulnerabilities and Exposures (CVE) database, a list of publicly disclosed vulnerabilities.
CVE was launched in 1999 by the MITRE corporation to identify and categorize vulnerabilities in software and firmware. MITRE is a nonprofit that operates federally funded research and development centers in the United States.
What is CVSS?
CVSS or Common Vulnerability Scoring System is a published standard developed to capture the principal characteristics of a vulnerability that produces a numerical score between 0 and 10 reflecting severity. UpGuard uses CVSS v3 for vulnerabilities where it is available and CVSS v2 for those pre-dating v3.
