What user permissions does UpGuard have?
UpGuard offers granular user permissions to help you control access to your account.
UpGuard offers granular user permissions to help you control access to your account. When you invite a user to UpGuard, you can set permissions for the specific user or designate custom permissions with a custom role. Using different types of roles ensures you can enact role-based access control to manage your account as you scale.
Note: Only one paid user can access the UpGuard platform with a Basic plan, and role-based access control is available starting with the Professional plan.
What user roles and permissions are available?
Vendor Risk and Breach Risk have three default user roles, each with different permissions:
-
Administrator is the account administrator and has the highest privilege for your account.
-
Standard includes access to most features available to your account (excluding administrator-level configuration features) by default.
-
Read-Only is available for restricted users to have read-only access to specified modules.
There are also two roles for Trust Exchange: Trust Exchange Standard and Trust Exchange Read-Only, which disable access to Vendor Risk and Breach Risk, and restrict the users' permissions to just those related to responding to security questionnaires and organising security documentation.
For some plans, account administrators can also create Custom roles with some permissions enabled and others disabled.
Account administrators can navigate to Settings from the sidebar navigation menu and then select the Users tab to review the permissions associated with each user. You can optionally set the Custom and Standard roles with administrative features but we recommend following the principle of least privilege when setting user permissions for a large team.
Account administrators
Users with administrative-level access (administrators and any other role that has been set with the option Can administer account) have access to additional features for managing the account and inviting additional users. Account settings, such as company branding, templates, custom labels, API key creation, and custom notifications are limited to users with administrative-level access.
For Professional plans and up, administrators can also access the audit log to review account activity. As an administrator, you can identify important events and filter them by time, event type, and user. This feature ensures that you can keep track of changes to your account and take necessary rollback actions if necessary.
Standard users
The default state for standard users includes access to Breach Risk and Vendor Risk (if your plan includes both products). By default, full access is enabled for most modules included in your plan. The standard role does not have access to Data Leaks.
Read only
Any user with administrative-level access can create an unlimited number of read-only users with restricted permissions. Read-only users have limited, read-only access that you can set for Breach Risk, Vendor Risk, and Trust Exchange.
Modules are only available if they are included in your organization's plan. Some modules, like Identity Breaches and Typosquatting, are only available for users that occupy a paid license seat, so adding those modules to a restricted user will change the user to a standard user.
Setting user permissions
When you add a new user or edit a user's role, you can set granular permissions for modules within the UpGuard platform.
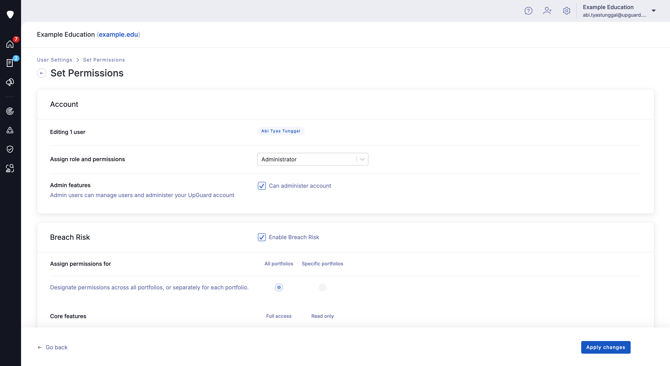
There are three sections to the Set Permissions page: Account, Breach Risk, and Vendor Risk.
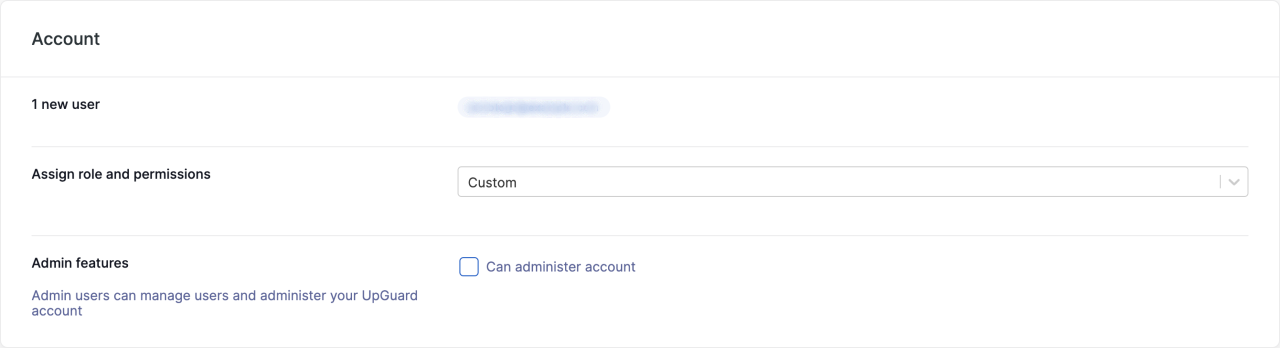
Account
In the Account section, you can select a role and decide whether the user(s) can administer your UpGuard account (invite users and access settings). This example sets a custom role that does not have administrative access:
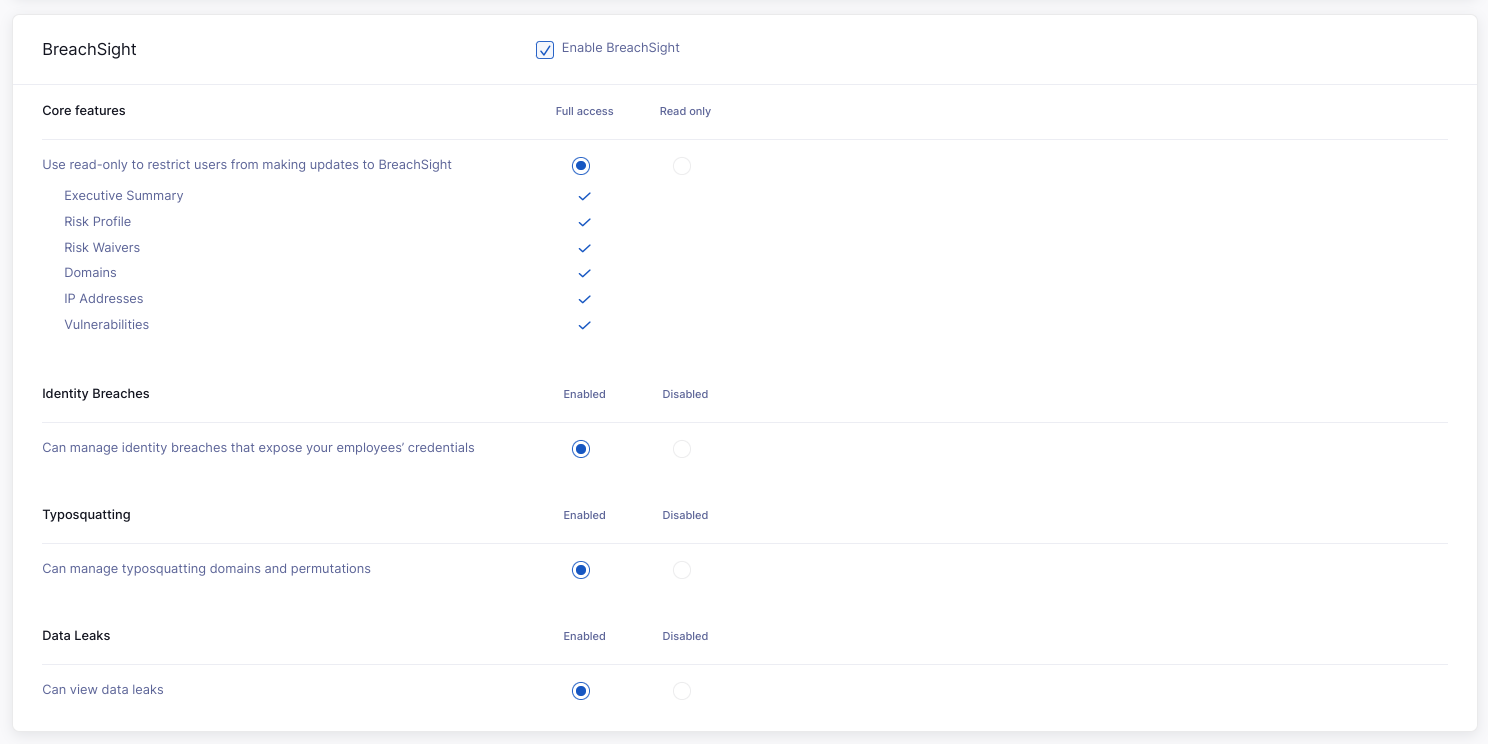
Breach Risk
In the Breach Risk section, you can provide or revoke access to Breach Risk modules. If you provide access, you can decide between standard (Full access) or restricted (Read only) access to the core features: Executive Summary, Risk Profile, Risk Waivers, Domains, IP Addresses, and Vulnerabilities. You can also enable or disable access to Identity Breaches, Typosquatting, and Data Leaks for plans that include those features.
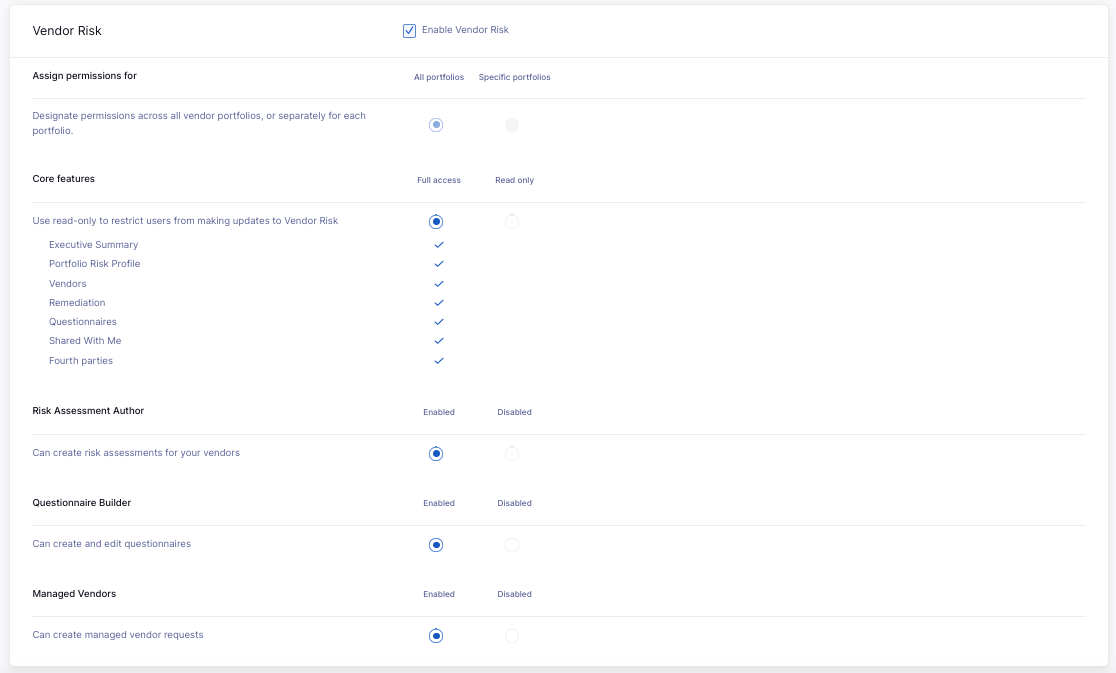
Vendor Risk
In the Vendor Risk section, you can provide or revoke access to Vendor Risk. If you provide access, you can decide between standard (Full access) or restricted (Read only) access to the core features: Executive Summary, Portfolio Risk Profile, Vendors, Remediation, Questionnaires, Shared with Me, and Fourth Parties. You can also enable or disable access to Risk Assessment Author, Questionnaire Builder, and Managed Vendors for plans that include those features.
Trust Exchange
In this section you can provide or revoke access to Trust Exchange. This allows you to choose permissions related to creating and publishing a Trust Center, organizing security documentation in your content library, importing questionnaires to answer, and more.

See also:
