Why isn't every vulnerability shown on my Risk Profile?
Learn about how vulnerabilities are treated in your Risk Profile versus your Vulnerabilities.
Every vulnerability shown in Vulnerabilities does appear in your risk profile but we treat unverified and verified vulnerabilities differently.
The relationship between the risks shown on your Risk Profile and the vulnerabilities shown in the Vulnerabilities section of the platform depends on whether we can verify that the specific vulnerability exists.
For context, UpGuard performs non-intrusive scans from outside of company networks, identifying potential vulnerabilities based on the information exposed through HTTP headers, website content, and open ports.
This often provides us with the specific software versions that an asset is running. We then check whether the exposed version has any known vulnerabilities. If it does, we add any known vulnerabilities to Vulnerabilities.
While we can often identify the specific version that is running, we're often unable to verify whether those vulnerabilities are exploitable. This is because we deliberately choose to run non-intrusive tests. The only thing we can verify in these situations is that a vulnerability may exist based on the exposed information.
These vulnerabilities appear as individual vulnerabilities tagged as unverified in Vulnerabilities.
However, in the Risk Profile, we group unverified vulnerabilities under informational risks based on the exposed software version. For example, the screenshot below shows an informational risk related to Exim Internet Mailer 4.92 which has two underlying vulnerabilities, CVE-2020-28018, CVE-2020-28010 and CVE-2021-38371.
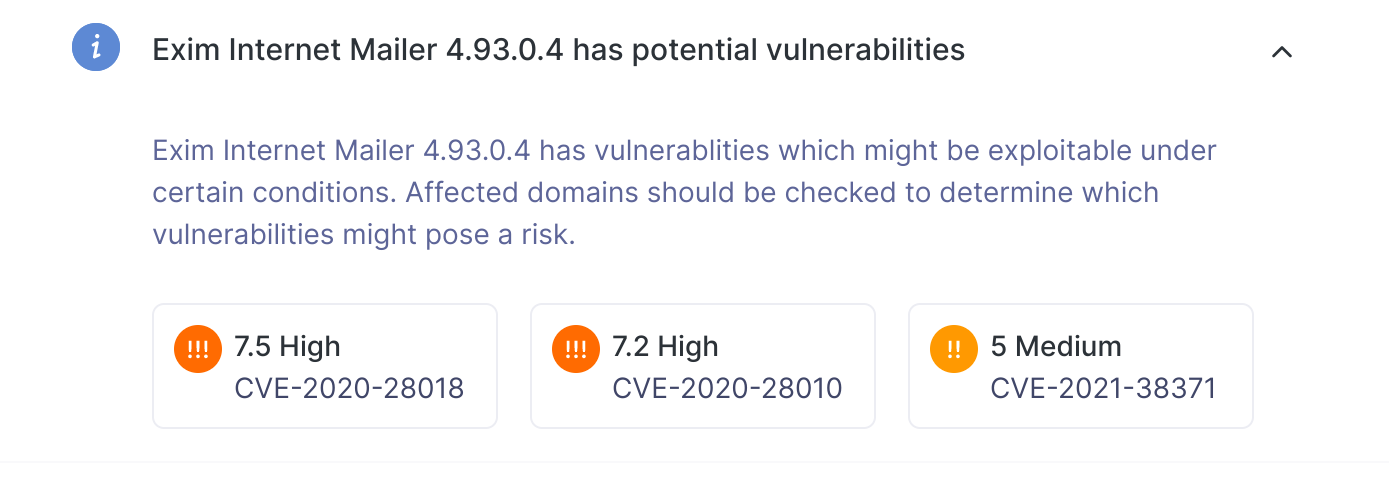
As you can see from the screenshot below, these appear as individual items in Vulnerabilities.

We do this because it's common for specific software versions to have more than one possible vulnerability. Grouping them together makes it easy to see what risks you may be exposed to and makes it easier to drive remediation efforts.
As an added bonus, it helps keep the number of risks shown on your Risk Profile to a manageable number. For the majority of organizations, the number of unverified vulnerabilities far outstrips the total number of risks across all other categories. And as we can't verify the exploitability of these vulnerabilities they appear as informational and do not impact your security rating.
In contrast, for some vulnerabilities, we can run non-intrusive tests to confirm that the assets are vulnerable to exploitation. These vulnerabilities are displayed as verified in Vulnerabilities.
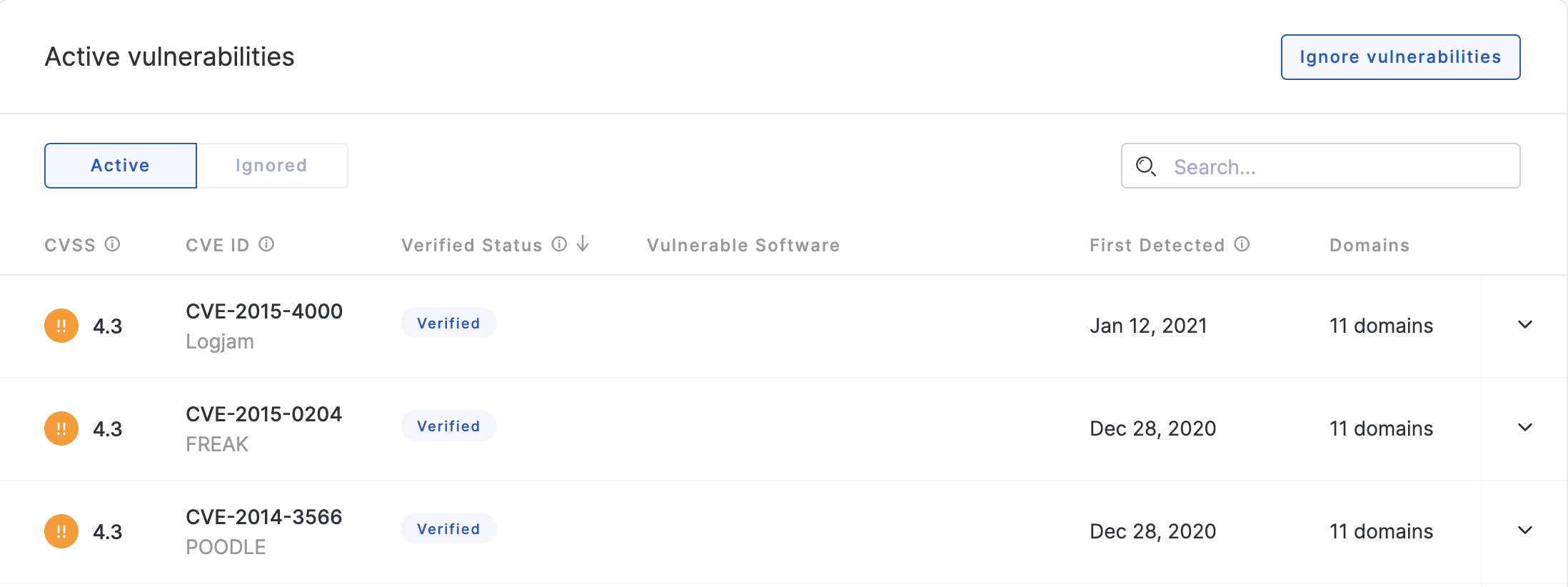
As we can determine the existence of these vulnerabilities, we know that they are negatively impacting your security posture. As such, we assign a severity each verified vulnerability and they appear on your risk profile as individual items. Verified vulnerabilities also impact your security rating.
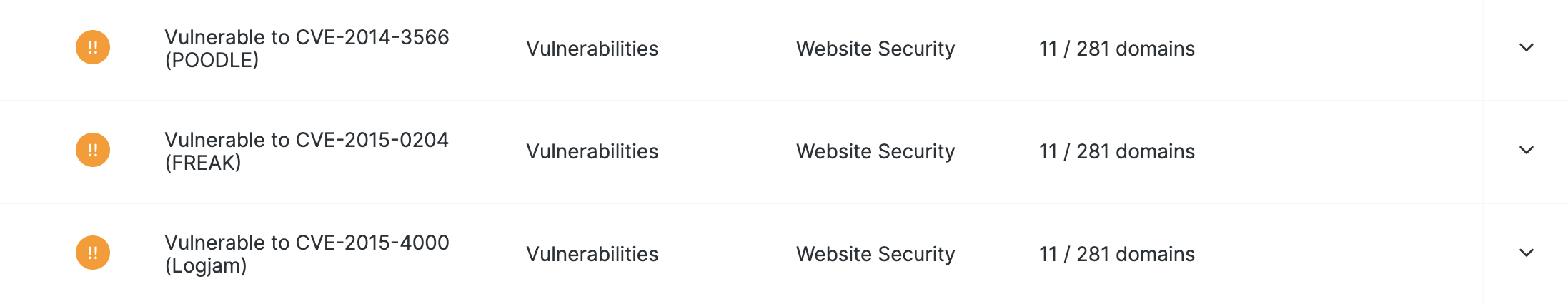
By making these distinctions, we ensure that you can focus on issues that we know are negatively impacting your organization's security posture while still providing visibility into all potential risks while keeping your Risk Profile at a manageable length.
See also:
