Identity breaches from ransomware leak blogs
Email addresses found in ransomware leaks are surfaced through Identity Breaches with a disclaimer that they are unverified.
UpGuard sources Identity Breaches from a variety of sources, including both proprietary collection methods and open information sharing in the security community. As with other forms of threat intelligence, confidence in the veracity of data is on a spectrum, from breaches that have been confirmed by the victim to those that have been falsified to fool security analysts.
Data released on ransomware leak blogs are somewhere in the middle– the data originates from an adversarial source, but analysis of the data can support or refute the claim that it originated from the target. Given that ransomware attacks are known to be real and widespread, we believe it is better to have more intelligence than less concerning potential data loss in one's supply chain.
For that reason, identity breaches sourced directly from ransomware blogs come with a disclaimer that the information should be investigated.
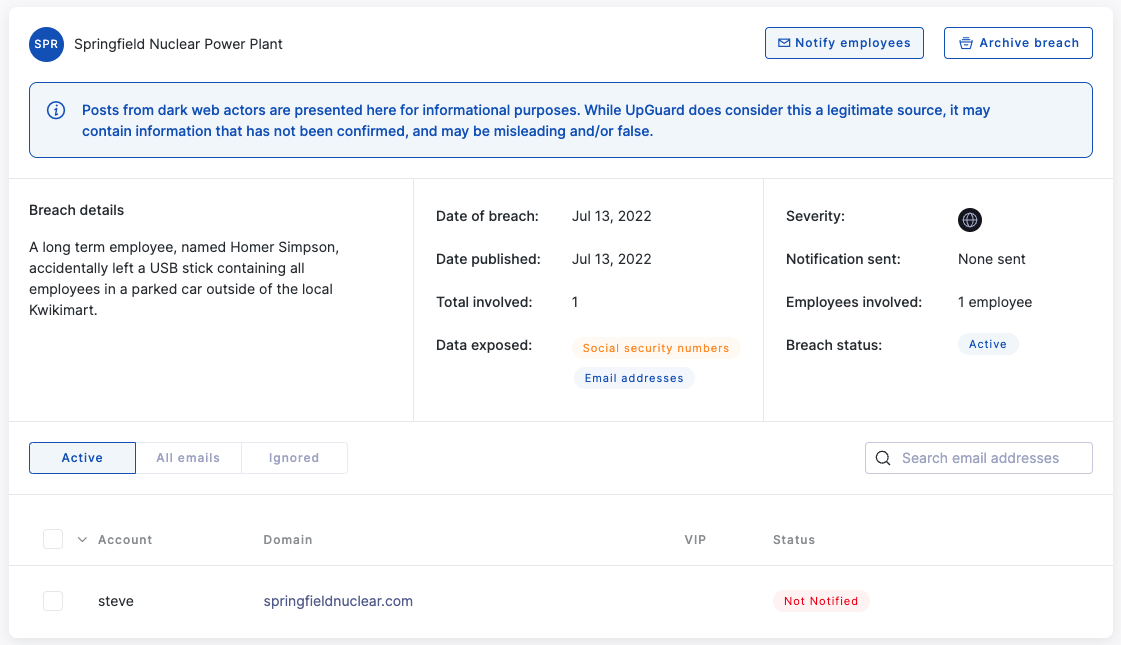
UpGuard monitors ransomware blogs for announcements of attacks and releases of data collections. When available, those releases are downloaded and searched for email addresses and indications of sensitive data classes. Those email addresses are stored as an Identity Breach and affected organizations are notified through that module. The original data set is then securely deleted.
As with other Identity Breaches, workflow features can help you manage your response and future notifications. When irrelevant mail identities are flagged– like noreply@yourcorp.com– you can set Identity Breaches to ignore this mail address in the future. Email notifications can be sent to identities you believe should be notified, and after all actions have been completed the breaches can be archived.
