Using the risk assessment framework in UpGuard
Benefits of using the risk assessment framework in UpGuard and the recommended approach
There are many actions you can undertake within the UpGuard platform to help understand the level of risk associated with your vendors. UpGuard offers a complete vendor risk assessment framework, neatly packaged in a single workflow, which allows you to compile all your risk assessment activities and information, assess and comment on the level of risk a vendor poses to your organization, and save as a point-in-time assessment for future reference and comparison. In this article, we will suggest a recommended approach for performing risk assessments to help you get the most out of this feature within the UpGuard platform.
Why use the risk assessment framework?
To ensure you have a complete picture of a vendor's risk profile you may need to combine information from different sources—including automated scanning, questionnaires, and additional evidence documents and links. If all these tasks are performed individually, it can be difficult to keep track and compile this disparate information into a state that gives you an overall picture of the level of risk a vendor poses to your organization and how this is changing over time. This is where risk assessments come in.
The risk assessment framework gives you a way to systematically work through all the steps required to perform a comprehensive vendor risk assessment. This includes the review of automated scanning results, questionnaire responses and other evidence provided by the vendor, and the remediation of any risks uncovered by these processes. This point-in-time view of a vendor's risk profile can be repeated at regular intervals to understand how risk changes over time.
The vendor summary page brings together all the evidence and activities together under the risk assessment framework. It helps you quickly determine the assessment state of the vendor, allowing you to manage your workflow and follow up on activities or schedule re-assessments as needed.
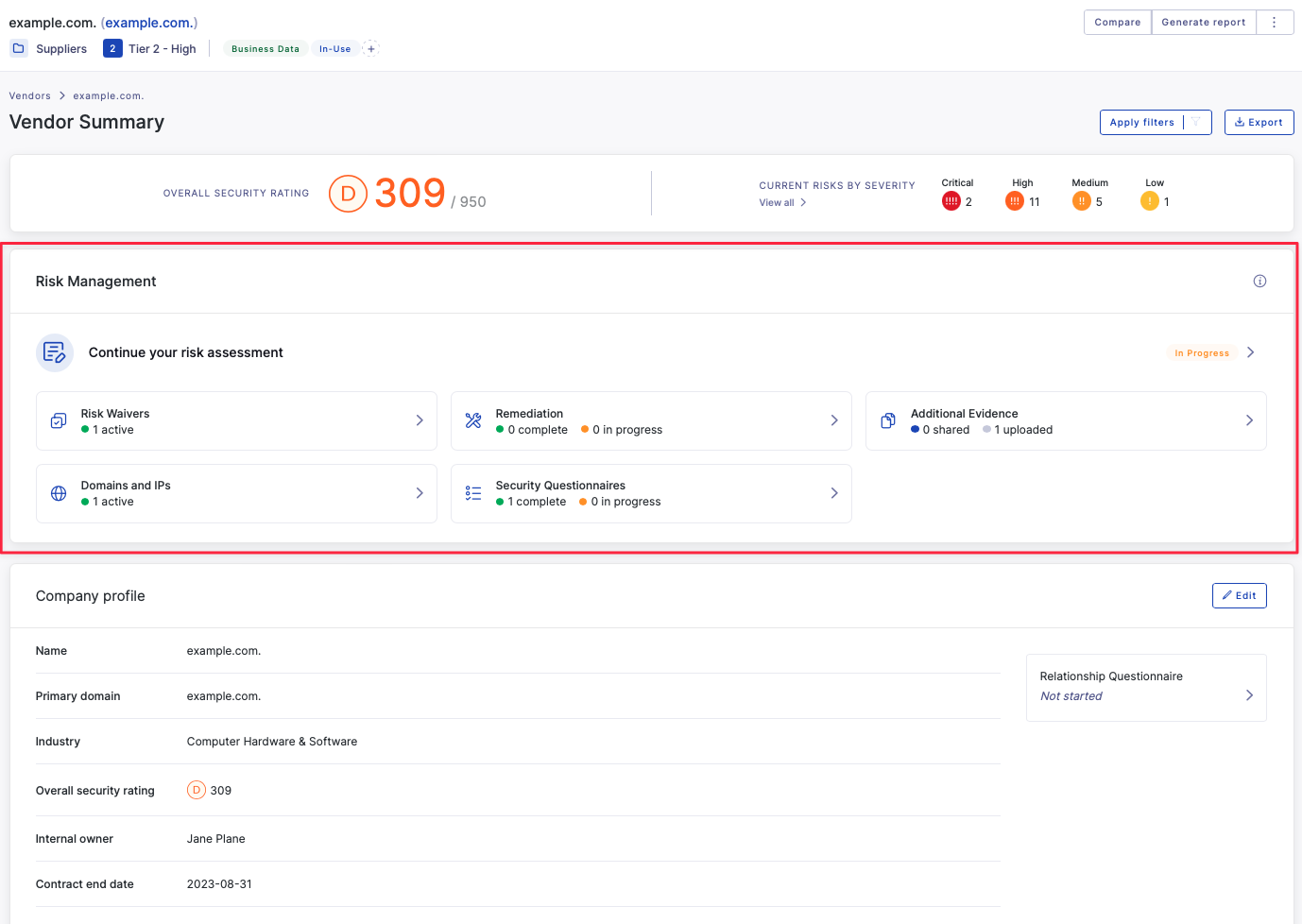
Recommended approach
UpGuard’s vendor risk assessment workflow is flexible enough to support different levels of assessment, from a quick review of automated scanning results to a full assessment including questionnaires and gathering additional evidence from the vendor. The following approach includes the full scope of a risk assessment. You might use this full scope for a tier one vendor, who poses a meaningful risk to your organization due to the data they will be handling. For a lower criticality vendor, or when a previous risk assessment has been performed it may only be necessary to undertake a portion of the steps.
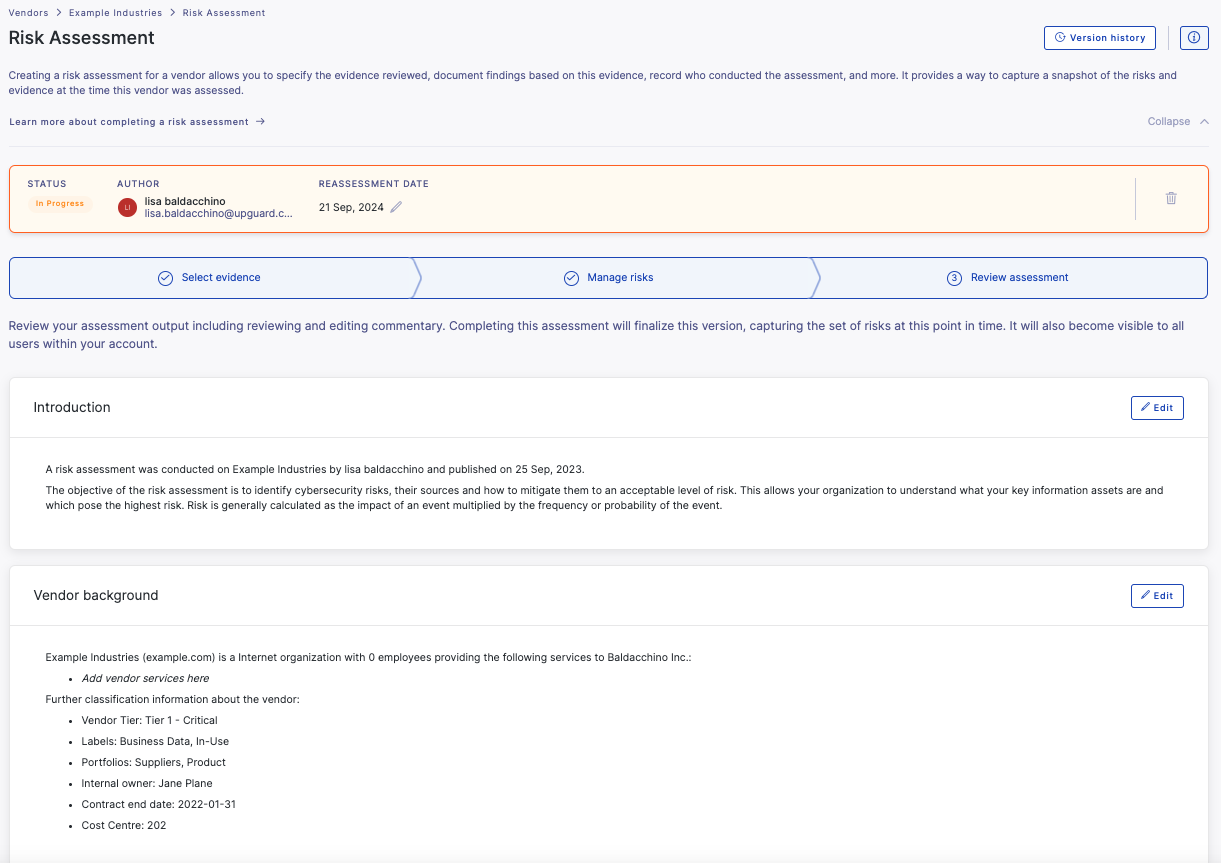
The risk assessment workflow comprises three main stages which are outlined below.
Stage 1: Select evidence
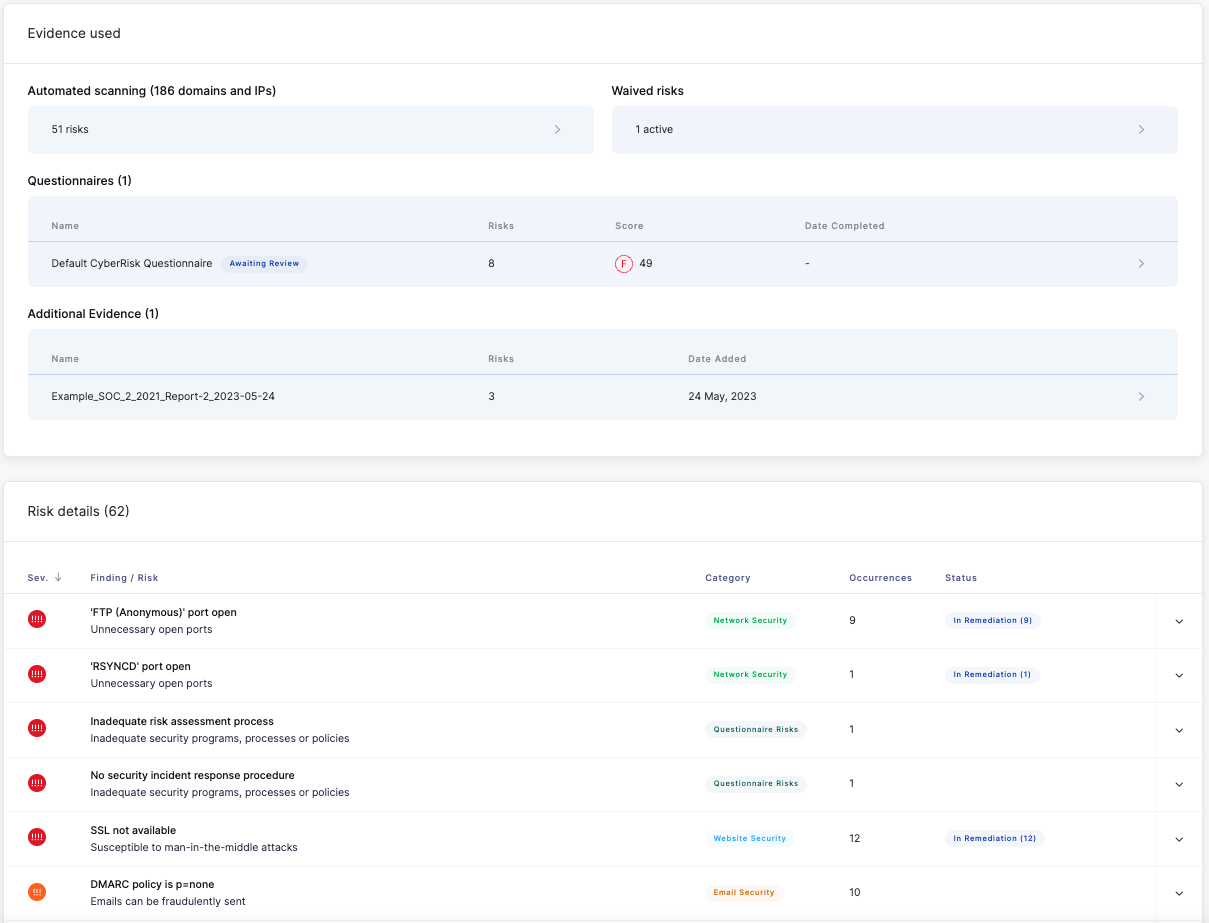
This stage is about collecting all the information together in order to assess the risk level of a vendor. The amount of evidence required is likely to vary depending on the risk they pose to your organization, usually managed through tiering your vendors, so you should decide upfront what you need based on this.
Decide whether you want to include your automated scanning results as part of your risk assessment. You would usually include automated scanning results unless you want to conduct an assessment based purely on vendor evidence such as security questionnaires and documentation (depending on the purpose of the assessment). Also you will not have any automated scanning results for a vendor with no web presence. You can also decide whether you want to include the effect of risk waivers in your assessment.
Send security questionnaires to help identify potential weaknesses among your vendors by gathering additional information that automated scanning cannot surface, such as information on security policies. Ensure you plan ahead to understand which questionnaires are appropriate or required for a particular vendor based on your relationship with that vendor, their tier (criticality) and industry. Ensure you set a due date for that questionnaire to allow for sufficient time to review and follow up on any information provided in advance of the risk assessment being completed.
Attach any additional evidence regarding the security posture of the vendor. This could include information which is publicly available, made available by the vendor through an UpGuard Trust Center, or documentation you have gathered through discussions with the vendor. Some useful examples would be SOC 2 Type 2 audit reports, any other regulatory audit reports or previous security assessments.
You can also include information found in publicly available Security and privacy pages in your assessment. These include pages identified and added by UpGuard, as well as custom links you have sourced and identified.
Stage 2: Manage risks
If you have gathered all the evidence in stage 1 ahead of time, it will make it easier to move on to reviewing and assessing the risks. During this phase you should decide on which automated scanning, questionnaire and additional evidence risks you believe need to be remediated or require other follow up action based on the nature of the risks, the evidence provided, and the criticality of this vendor.
You can request remediation on a risk or group of risks as part of this stage of the risk assessment workflow. Make sure you set a due date for remediation which is in-line with your assessment timelines, but also allows sufficient time to take appropriate actions to remediate the risks. Provide sufficient detail in your message to the recipient so they understand why you need this risk to be remediated.
You can also add commentary against individual risks in this step. This could include compensating control information or mitigation activity that is underway. These comments are included in the final risk assessment and report, but not stored against the risk profile.
You may also choose to waive a risk if the vendor has provided sufficient information about the controls they have in place, which can be done within the risk assessment by expanding out one of the risks.

Stage 3 Review assessment and commentary
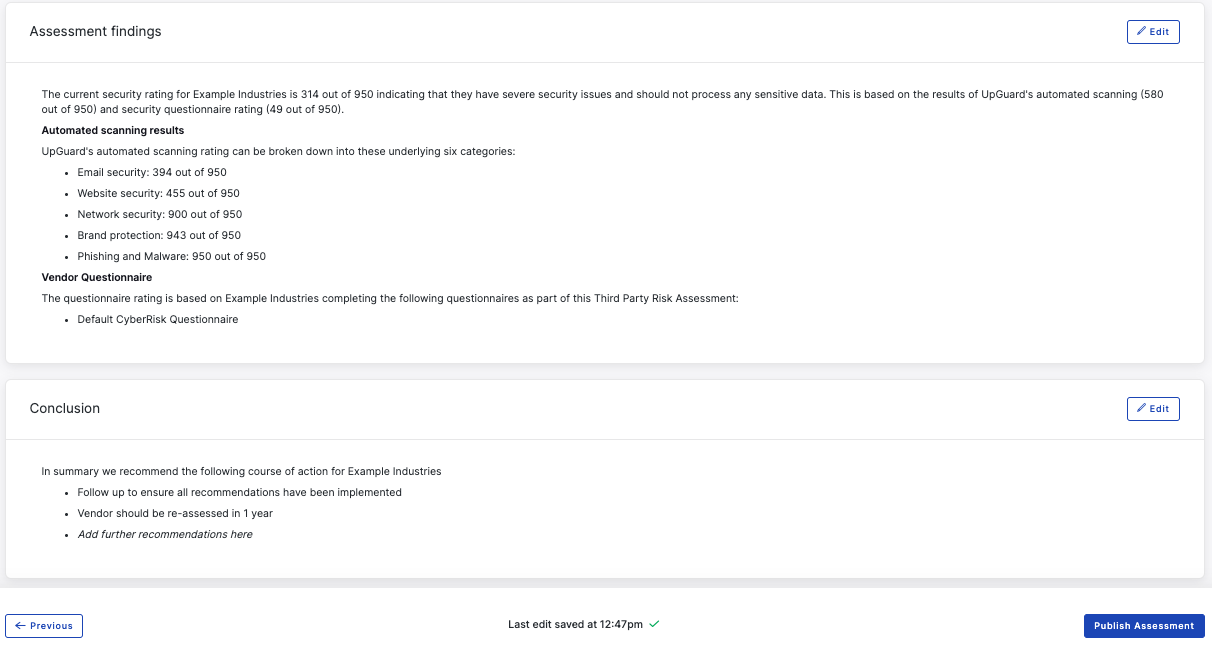
Once you are satisfied that you have assessed all evidence and risks and compiled all the responses from your vendor, use the commentary sections to summarize the results of your risk assessment.
The commentary in your risk assessment will be pre-populated based on the customizable template found in Settings>Templates>Risk assessments. UpGuard provides a pre-defined default template which uses merge tags so you can pre-populate your risk assessment with important information like vendor tier and attributes, and vendor rating including category breakdown. To give you the flexibility you need to present the information in the way you need the template is broken into 4 sections: Introduction, Vendor Background, Assessment summary and Conclusion, each of which can be customized according to your specific needs.
In the review step you can:
-
Review the included evidence, including following up on any outstanding action items such as incomplete questionnaires or unapproved risk waivers
-
Review your included risks and any comments you added to individual risks, follow up on any open remediation requests and note any further action or remediation required
-
Review and edit the commentary which has been automatically generated based on your template, and add any additional vendor-specific comments and recommendations.
Your assessment should take into account the Tier and level of risk that vendor poses to your organization, and include any key pieces of evidence or key risks, any follow-up actions you are recommending to improve the risk profile for this vendor, and any overall recommendations for dealing with this vendor.
Plan for reassessment
Once you've reviewed and added any additional commentary you can publish your assessment. For vendors you have an ongoing relationship with, set a reassessment date, taking into account the level of risk this vendor poses to your organization, as well as your operating cadence for performing risk assessments.
Performing regular risk assessments using this framework should ensure you have a comprehensive and common understanding of your vendors’ security posture, a central place to find any information pertaining to their risk profile, and a clear picture of how this has changed over time.
For detailed information on performing risk assessments within the platform, learn more about how to complete a risk assessment.
