What are Known Exploited Vulnerabilities?
UpGuard annotates vulnerabilities that are being actively exploited by attackers.
Out of all known CVEs, only a small percentage are actively being exploited at any given time. Being able to identify known exploited vulnerabilities, or KEVs, allows you to prioritize remediation activities to stop active threats.
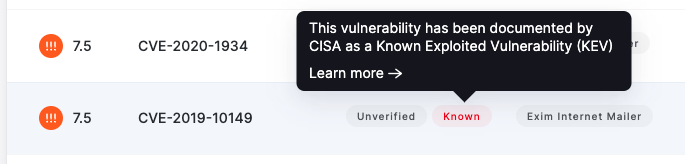
When UpGuard detects a vulnerability that is in the CISA catalog of known exploited vulnerabilities, any instances of that vulnerability will be visually flagged with a label that says "known."
This can be seen in the list on the Vulnerabilities page:
And on the risk details panel for domains and IPs:
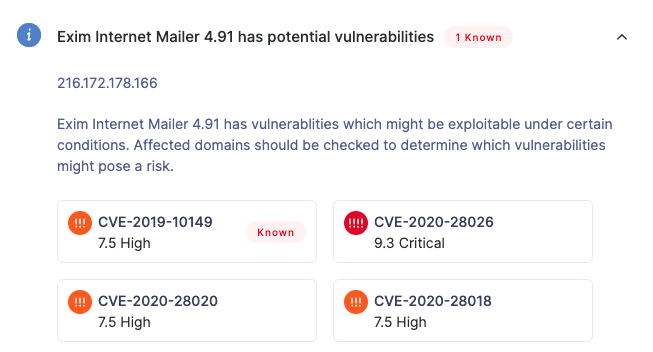
UpGuard includes the "known" label for both verified and unverified vulnerabilities. In the context of UpGuard's vulnerability detection, "unverified" means that the vulnerability is known to affect the detected software version, but that there may be patches applied that cannot be confirmed without intrusive scanning. When you know that a system has been patched against a vulnerability, you can "ignore" that vulnerability to indicate you have investigated and know it does not affect that system.
A timely response is important for actively exploited vulnerabilities, so you can configure your notifications to inform you whenever vulnerabilities are detected in the KEV catalog.
It's important to note that not all vulnerabilities in the KEV catalog can be detected by an external attack surface management platform like UpGuard. For example, some KEVs pertain to exploits in Office documents, which are not part of an organization's external footprint.
