What is infostealer malware?
Learn about infostealer malware, and how to view, understand and conduct remediate using UpGuard's Identity Breaches module.
The Identity Breaches module tells you when your employees are at risk of being targeted for account takeover attacks. One way is by notifying you when your employees' business email addresses have been found in data breaches at other organizations. Another way is by notifying you when those business email addresses have been found in collections of credentials captured by malware.
In this attack vector, attackers have distributed malware to some device that the person is using—a computer or mobile device—that logs their information as they sign into web services. This class of malware, designed to capture users' information, is called "infostealer malware". The malware then transmits that captured information back to the malware operator, who will try to sell it to other threat actors looking for stolen credentials.
When UpGuard has recaptured those stolen credentials from threat actors, you will see an Infostealer Malware event in the Identity Breaches feed.

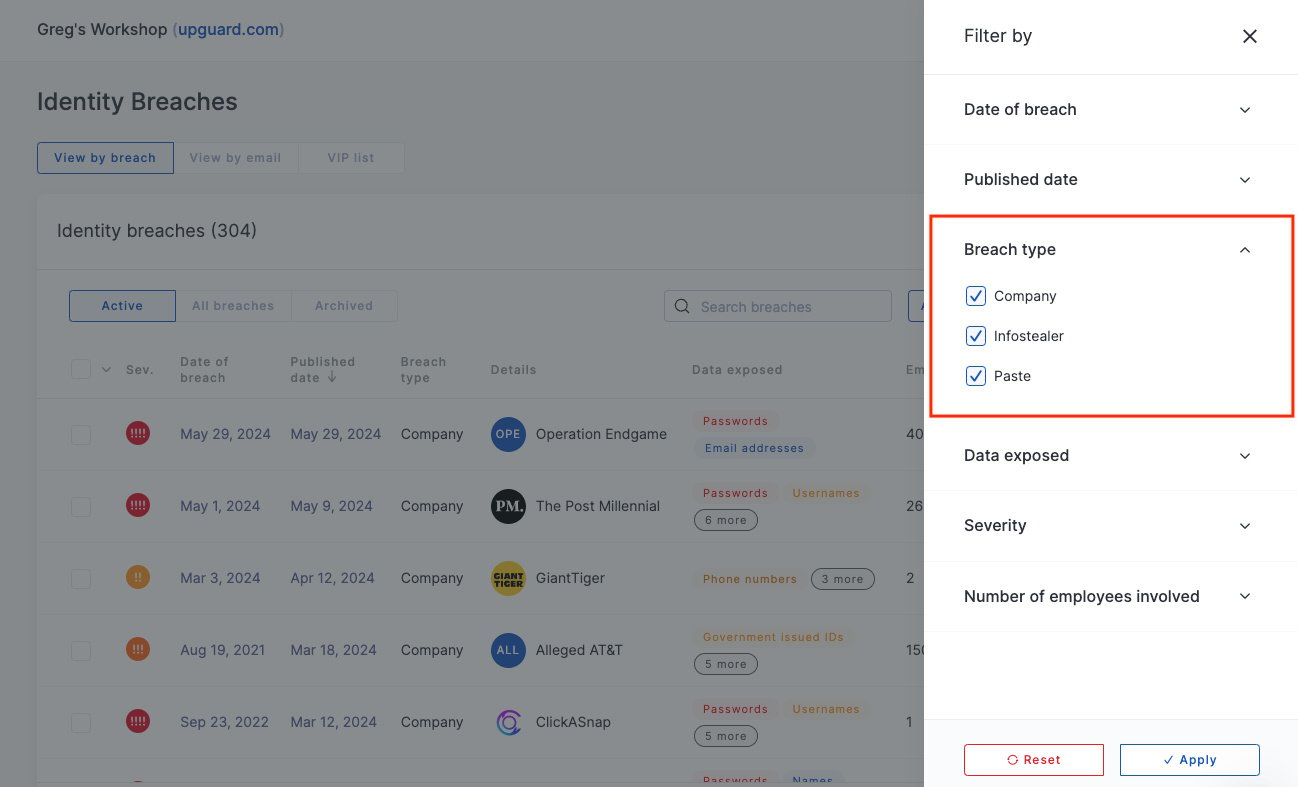
To view only infostealer breaches, you can filter on the "breach type" property.
Understanding infostealer events
When a business identity shows up in the infostealer logs, it does not necessarily mean that user's work computer has malware—it means that they used their work identity to log in to some service on a device that has malware. That device might be a personal computer, shared computer, phone, tablet, or anything else that allows a user to log into a web service.
Similarly, the service they are signing into may be a personal account they have signed up for using their corporate email address—like an Amazon, Spotify, or retirement fund accounts—or it may be a service related to their job, like logging into Microsoft Online or other SSO provider.
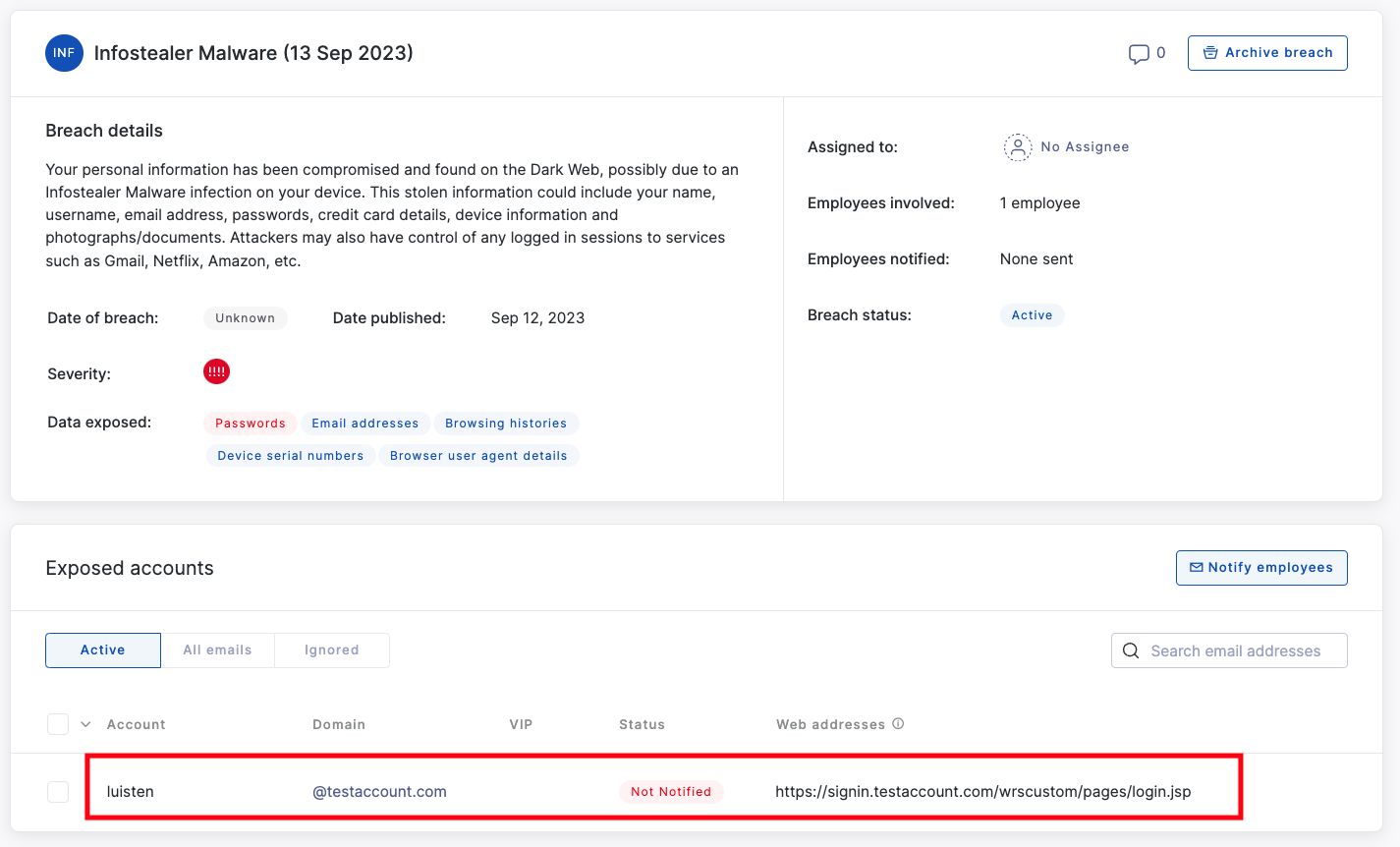
Remediation
When your users' identities show up in infostealer events in Identity Breaches, you can use Identity Breaches' workflow capabilities to assign the event, track investigation, and close the case.
Some recommended actions, depending on what is feasible:
-
Ensure none of the user's known devices have malware
-
Advise or force the user to rotate the credential
-
Investigate the user account's behavior to determine whether the credentials were abused
