User Risk: Overview
What is User Risk
User Risk helps you manage the human risk in your organization by combining data with real, actionable insights that help you develop and enforce policy, while providing real-time behavioral nudges for users to build secure habits across your workforce.
 User Risk gives you
User Risk gives you
- Visibility and insight. Via an integration with your employee directory and a dedicated browser extension, User Risk gives you insights into your team’s app usage, Shadow IT and identity breaches.
- The ability to create and enforce policy. Set custom rules for application usage. These rules can automatically trigger alerts and inform real-time coaching, transforming your security policies from a document into a consistently and measurably enforced program.
A browser extension provides users with real time cybersecurity insights into the pages they’re visiting, and, depending on settings, can help them understand how their behavior impacts their security score, and track trends over time.
How User Risk works
User Risk gathers information in two ways:
- By connecting with your company directory: this tells User Risk where your employees are using their company credentials to log into an application via SSO.
- Via a browser extension: the extension tells you what apps and sites people are using (regardless of logins or credential usage). More on the extension’s usage tracking criteria.
Value
- Workforce risk visibility: Get a clear view of each employee's full risk posture.
- Automated governance: Proactively enforce SaaS and AI policies.
- Behavioral coaching for your team: Drive secure habits with in-workflow coaching.
Navigate User Risk
Navigate User Risk from within UpGuard.
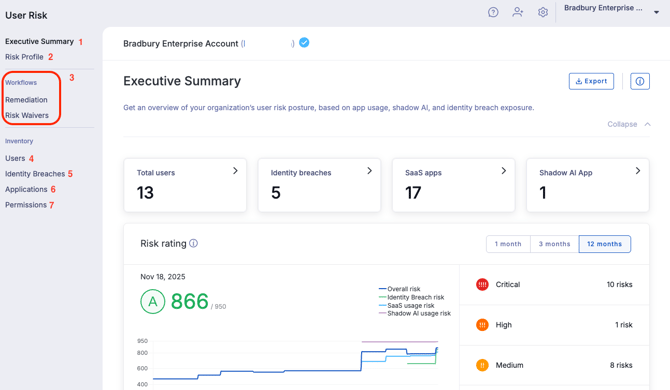
- Executive Summary. Gives you high-level insights using data from across User Risk, and helps you dive into the details to explore further. You’ll see: how many users are in the platform, their risk ratings, the number of SaaS apps identified, a risk overview, and more.
- Risk Profile. Highlights all risks identified via User Risk (e.g. identity breach risks, SaaS usage risks, etc), their severity, date of detection and number of affected users.
- Workflows. Shows risks in remediation or risk waiver workflows.
- Users. A user-centric view of User Risk activity, focusing on your team members, their security rating, and their app usage.
- Identity Breaches. Lists all detected identity breaches associated with your team, the breach severity, and provides details about what data was exposed.
- Applications. A list of the apps and sites that User Risk has detected across your workforce. Explore apps and manage policies from here.
- Permissions. A catalog of all of the permissions your users have granted applications. Explore permissions that users have granted and assess whether they are appropriate for your organization.
